What is hashing? This is a method used to confirm that a file has been unchanged. Hashing a file is a one direction process. The result of the hash can not be reversed to show the original file data. The result of the hash or checksums are compared to validate the file is identical to the original. If the checksum is different then the file has a problem, do not use it.
Hashing Methods
There are primarily two (2) hashing methods used.
- MD5
- SHA256
These hashing methods are the most commonly used for checking the files integrity. Here is a list of other types of hashing algorithms. Secure Hash Algorithms – Wikipedia
How to perform this method
If you are using Windows Operating System you will need to use Powershell to follow along.
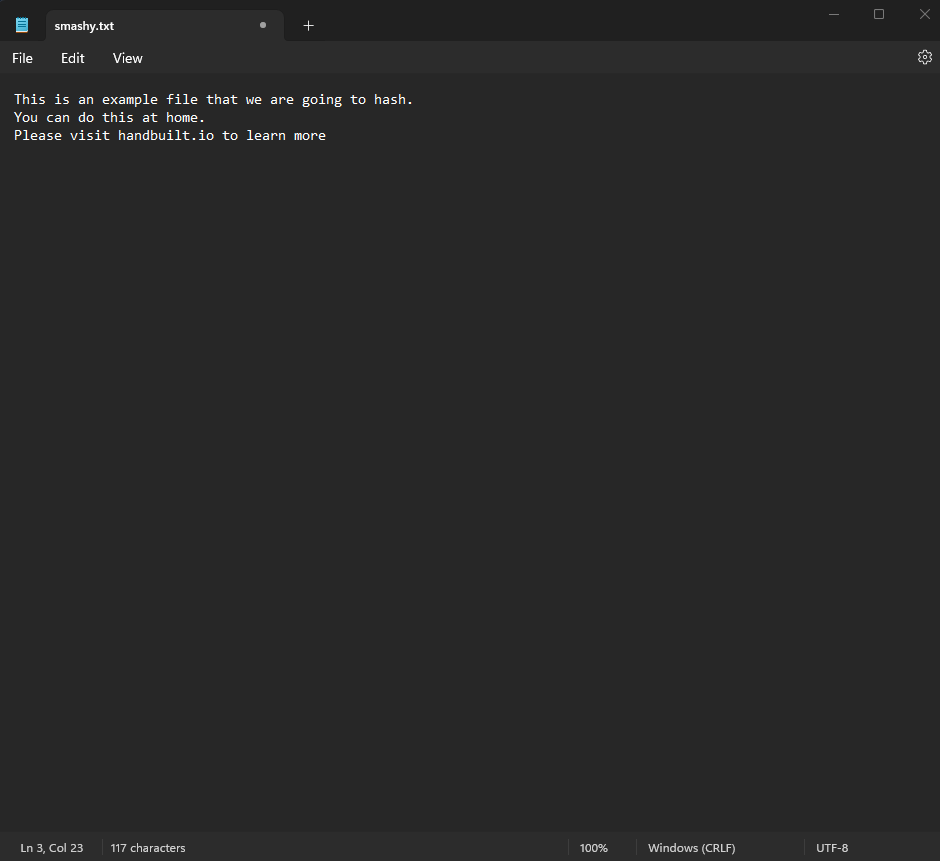
Lets first make two text files. The first one will be called, “hashy.txt”
Inside hashy.txt please enter (You can enter whatever you want):
This is an example file that we are going to hash.
You can do this at home.
Please visit CyberBits.io to learn more
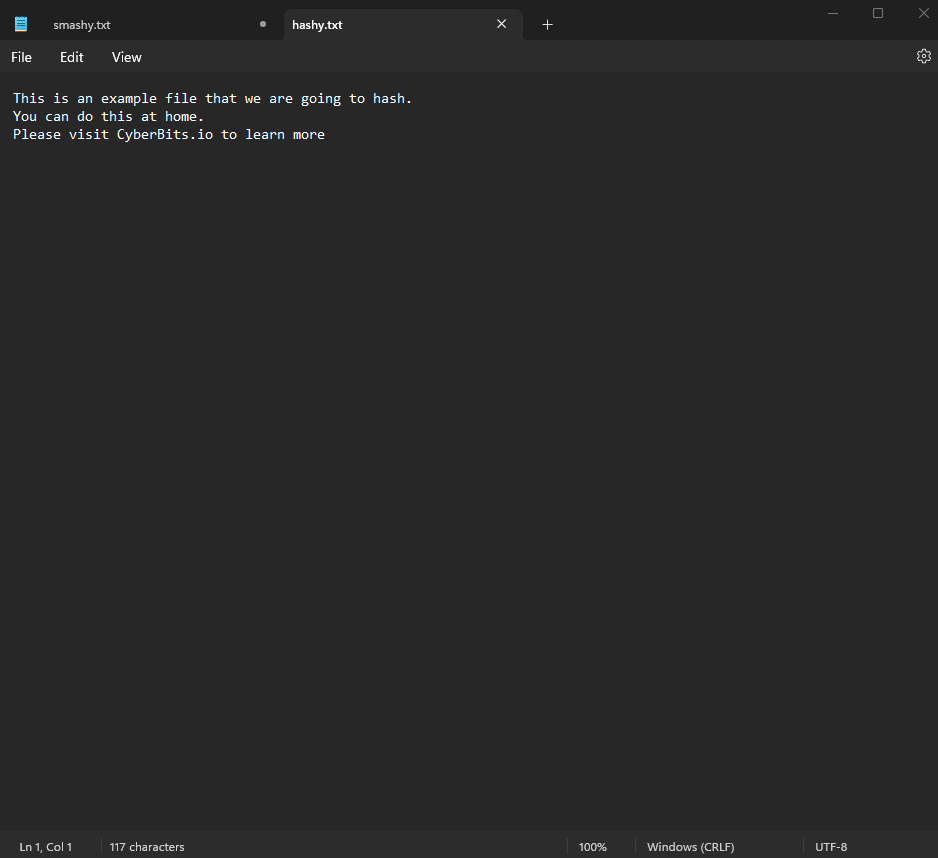
The second file will be called, “smashy.txt”
Inside smashy.txt please enter (You can enter whatever you want but just change one word):
This is an example file that we are going to hash.
You can do this at home.
Please visit handbuilt.io to learn more
Save both of these files in the same folder to make it easier to navigate to them.
Now open Microsoft Powershell.
Using Powershell type in:
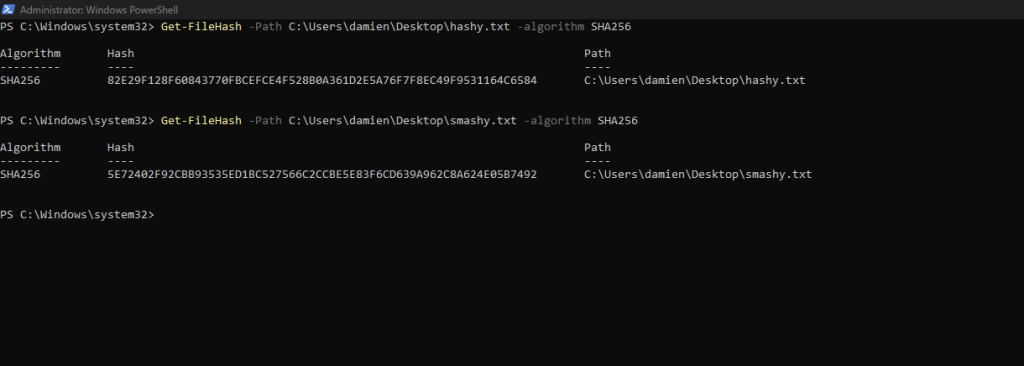
Get-FileHash -Path C:\thepathtoyourtxtfile -algorithm SHA256
Do this for the hashy.txt file. This will give you the SHA256 hash for the hashy.txt.
To see how amazing this is, do the same with smashy.txt. Only one little section was changed with hashy.txt and you would assume that it would only change a few of the characters in the hash. It actually changed the output hash completely.
Remember, whatever you put into the hashing algorithm, the ending hash will always be the same length. If your file is 100mb or 4mb you will get the same amount of output bits.
You can play around with changing lettering or even adding words to the file. Each time you make any change to the file you will discover that it creates a completely new hash value.
That is how to use hashing to verify a files integrity in a nutshell, or should I say Powershell.
Checking the integrity of a downloaded file
What if you want to download a file from a location online or someone provided a file to you. How do you ensure that it was not tampered with or changed prior to you receiving it?
When I say tampered with, I mean that a virus or trojan was attached to the file. By using hashing the file, you could see if the file is different than the one that was sent. The Hash will tell you if it’s completely intact as it was sent or it’s modified. You will not know what modification was made but you will know it’s not the same.
The trusted provider of the file will need to produce the file hash from their end. They will use the same method above to navigate to the file location in PowerShell. Then they will use the hash algorithm to produce the hash.
Then they will send you the file and the hash. They will need to include whether the algorithm is SHA256 or MD5 so you know what algorithm to use.
Then you would just need to check the hash the same way we did above.
Get-FileHash -Path C:\thepathtoyourfile -algorithm SHA256
If the hashes match then you know the File Integrity is Confirmed.
If the hash is not the same as provided to you from the vendor, then you know the file is either corrupt or has been tampered with.
An example of a hash provided by a vendor
A great example of a vendor that provides their hashes for their installer is Virtual Box. If you navigate to virtualbox.org and go to their downloads page.
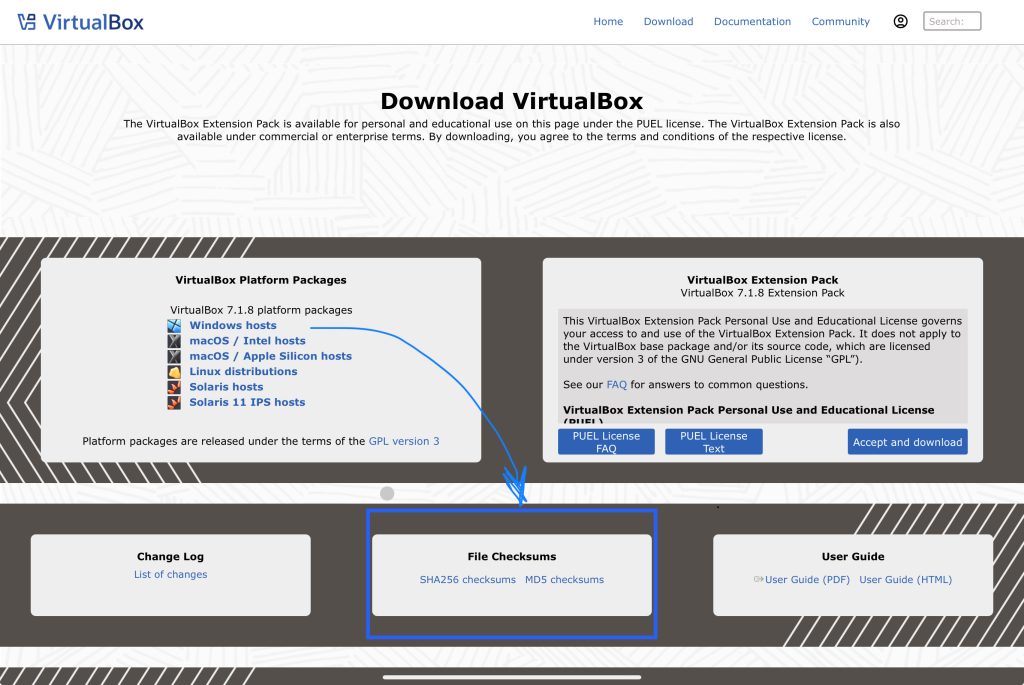
You will see the different installers for the supported operating systems. If you look below the list of installers you will find they provide links to a hash file for the SHA256 algorithm and the MD5 algorithm.
When you download either of the algorithm files you will get a list of the hash’s for each installer that they provide.
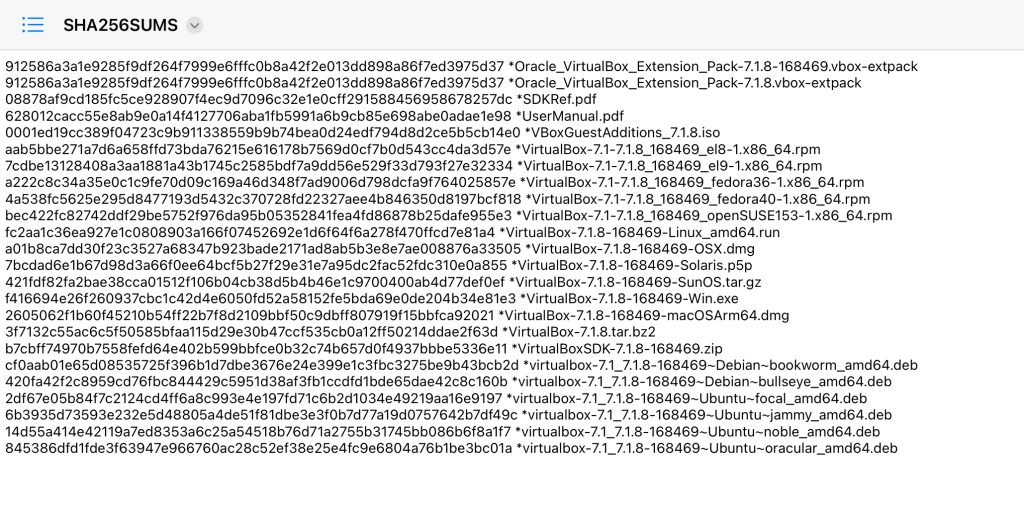
You are able to open the provided algorithm files in a text editor. I opened them on my Windows computer with Notepad. I did change the file extension to .txt so that it would show up as a note file. I also opened this file on my iPad but also had to rename the file to have a .txt extension.
Hash it out: Final Thoughts
File integrity may not be fun and flashy, but it is a crucial step in ensuring the file you install on your systems are unaltered.
By using simple hash checks like SHA256, you gain a powerful way to detect data integrity flaws. Whether you are using this to verify a downloaded app, data file or photos, hashing will give you peace of mind that your data has not been modified. Don’t hope for integrity but hash it out to be sure.